
As we said in our article at the end of June, love it or hate it, remote working is here to stay. The coronavirus pandemic has acted as a catalyst rapidly forcing many companies to embrace a work-from-home model. With no miracle cure for COVID-19 on the near horizon, for many employees, working from home is likely to be the new standard.
Time to reset traditional thinking on how we work
Already, many people who have been forced to work from home are finding they’re just as productive and collaborative as they were in office buildings housing thousands of workers. And they are now questioning why they had to go into the office in the first place.
Likewise, employers across industries are seeing the business benefits of remote working which include heightened levels of retention, productivity gains, access to a larger talent pool, and savings in terms of office floor space rental fees. As we near close to six months of supporting the work-from-home model, many businesses have formed the view that remote working is here to stay.
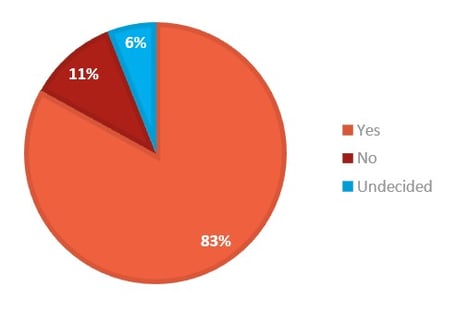
This sentiment is clearly reflected in the data we collected through imei’s online poll. We asked whether businesses intend to allow staff to continue to work from home after the restrictions lift – and a conclusive 83% answered in the affirmative. Only 11% of participants answered “No”, with the remaining undecided.
While COVID-19 has prompted employers to move away from traditional thinking on set hours and office environments, supporting remote working requires new thinking on data security measures and essential communications and collaboration tools.
Equipping your business for remote working
Ensuring your business is super-productive, efficient, and competitive with all your people working remotely, calls for serious reinforcements in your cyber-security posture – including adding new layers of security protocols for remote work.
As we described in an earlier post on 3 keys to establishing a secure and productive work environment, supporting a remote working program requires:
Provisioning desktops and devices
Use an enterprise mobility management (EMM) application to provision desktops and devices to give employees secure remote access to devices, data, business applications, and UC tools
EMM helps to centrally managing large deployments of devices with minimal IT resources – allowing companies manage remote technology, devices, apps, content and security.
Securing endpoints and data
Set up a variety of new security measures and robust user controls, including
ensuring all endpoints are secure, patched, and up-to-date, and that the systems will only run authorised applications.
Whenever an employee is working remotely, they should be accessing your organisation’s network and resources via a virtual private network (VPN) to prevent core systems being compromised via the internet.
Providing end-user support
Boost your help-desk support team to meet increased support requests by moving staff internally to bolster the team or by partnering with an outsourced provider. Provide self-service options so that employees can manage routine tasks such as changing their password if they're locked out of the system and ensure support is available through multiple channels, including bots, chat, email, and phone.
Essential communication tools
To get the best from remote workers strong communication is everything. Allowing your people to communicate and collaborate across multiple devices increases efficiency, productivity and ultimately, business results.
Unified Communications brings together instant messaging, voice, audio and video to support flexible instant connectivity regardless of location, time zone or other various factors. Facilitating the internal collaboration required in a modern workplace, UC ensures your people can be contacted no matter where they are.
Prioritising data security challenges
As we explained in our post on securing sensitive data, with the shift to new working it’s essential to prioritise data security challenges using modern EMM tools which include:
- Mobile Device Management (MDM)
- Mobile Application Management (MAM)
- Mobile Identity Management (MIM)
- Mobile Information Management (MIM)
- Mobile Content Management (MCM)
Free checklist to maximise remote working
For help setting up your business to run at optimal levels with a remote workforce, download our Work from Home Communications Checklist. This free tool helps you cover all your bases, taking you through equipment checks, network requirements, and support services.




