
As mobile security, data protection and privacy have become hot topics, one area of increasing focus is mobile app security and app data leakage. imei partners with best-in-class mobile security technology providers such as Wandera, who provide some valuable insight in this blog post.
You probably hear a lot about leaking apps but do you understand what’s actually happening when an app leaks data? You may have some leaking apps on your phone right now. In fact, a recent study reports 1 in 50 iOS apps on corporate devices leak data. Considering the average person has 140 apps installed on their devices there are a few holes in your armoury. How are you supposed to identify app leaks? Most of the time you won’t know until it’s too late.
What exactly is happening when an app leaks data?
App leaks involve the unauthorised or unintentional transfer of sensitive information from a mobile device to an Internet service. It is often the result of security measures being deprioritised in the app development process. App leaks on a mobile device expose sensitive information when an app developer or web programmer fails to use HTTPS to securely communicate over the network.
By not protecting the data, the app developer is essentially making the data available to anyone who utilises the same network as the device with the vulnerable app. This can happen with a man-in-the-middle attack. Once the information is captured it can then be used by a bad actor to break into other accounts or sell on the dark web or to weaponise a larger attack on a corporate network.
Categories with the most app leaks
Analysis of the 200+ app leaks uncovers a wealth of insight about the type and origin of app leaks. Categorising the content by its type reveals that more leaks were present in certain segments than others.
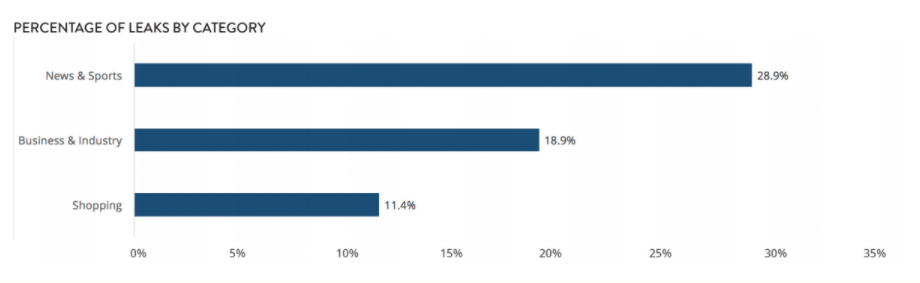
Volume of app leaks: high-risk categories
Alarmingly, news and sports websites were the most commonly featured category among those leaks identified. Perhaps even more worryingly, business and industry services accounted for almost 19% of every leak discovered.
News and sports websites, which include some of the best-funded and well-staffed organisations in the world, pose a far bigger risk than many CIOs may expect. The same is true of business and personal services, a category that comprises of company websites and other corporate entities.
Shopping apps and sites typically require a great deal of personal information due to the nature of the content. In order to make purchases, users must hand over PII such as credit card information and their physical address. That such a high proportion of leaks have been discovered in these types of services should be an alarming signal for security leaders.
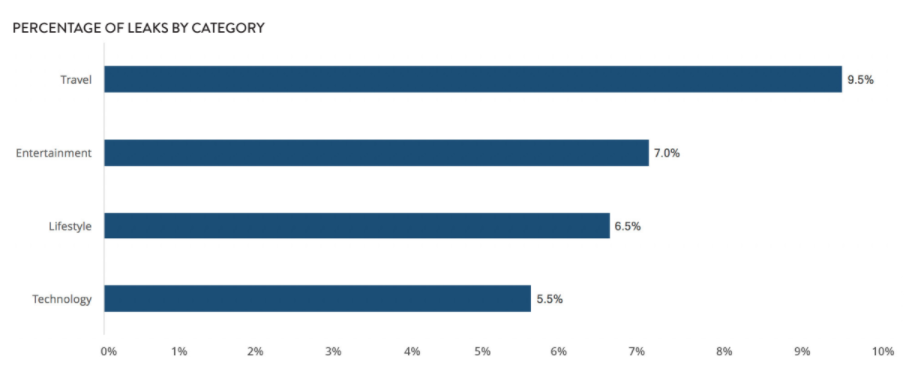
Volume of app leaks: concerning categories
A significant number of leaks were identified in travel websites, accounting for almost 10% of all the leaks discovered. Entertainment, lifestyle and technology services – each mostly used for recreational purposes represent 19% between them.
Mobile travel applications are frequently used at work, as employees spend an increasing amount of time overseas and in transit for business. Leaks in journey planning, seat reservation and ticket booking features for services including train operators and airlines were among those discovered by Wandera.
Lifestyle and entertainment categories span everything from Buzzfeed to Tinder and are unlikely to be used for work purposes, apart from in certain industries. On the other hand, technology applications and websites are primarily used to meet professional needs, such as Google Analytics for web insights or Adobe’s online services.
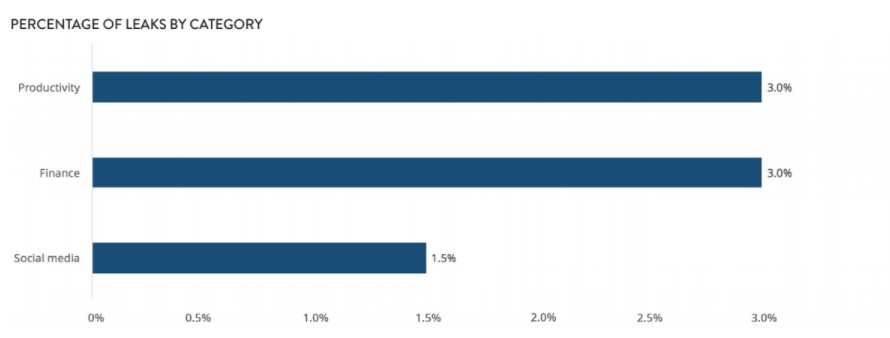
Volume of app leaks: surprising categories
Although the total volume of leaks spotted in the social media, finance and productivity categories was lower than elsewhere, that there were any at all will likely be of some surprise to many CIOs. Productivity tools are critical to the mobility programs of most enterprises and without platforms like Microsoft’s Office or Evernote, there might be far less need for smartphone-enabled workforces in the first place. Around 3% of the identified data leaks were in this category: troubling news for security-conscious mobility leaders.
Leaks in social media sites were rarer, but just 10 apps in this category – including Facebook, Twitter, Instagram and Pinterest – constitute the lion’s share of this usage and many of them have already had their security scares and learned from them. Stock-checking and banking services were similarly secure, but any leaks whatsoever in this category should be considered extremely risky due to the sensitive nature of the data involved.
PII that is most exposed by app leaks
Not all data leaks are equal. While of course none are desirable, those that expose financial information could be considered as more sensitive than the risk posed by leaking email addresses. However, all PII leaks are extremely dangerous, and all forms of exposed data may be used as part of a wider attack.
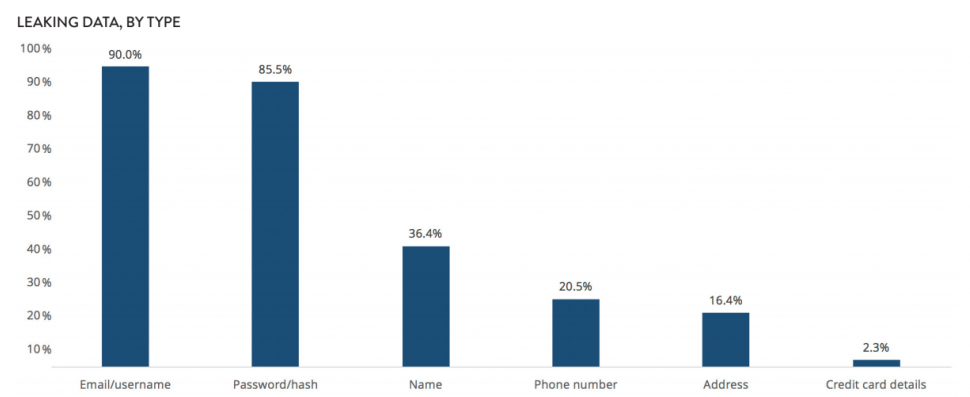
The pattern here is clear. The more perceived sensitivity the data has, the more security measures are put in place – hence credit card data being typically more rigorously protected. This is largely driven by the threat of fines for regulatory non-compliance and the spectre of legal liability for identified leads.
Despite all advice to the contrary, because of the overlap that this profile information inevitably has with multiple other services and systems, including log-ins to the enterprise network, these seemingly minor leaks can be catastrophic.
Indeed, for many attackers, app leaks on enterprise devices can be the ‘keys to the kingdom’. In most cases, usernames and passwords are sufficient to provide full access to a user’s online account. Even if the other bits of information did not leak, an attacker with access credentials could bypass any protections that are put in place and gain full access to the account.
What’s even more alarming is the fact that the other personally identifiable information leaked as well. Research by Carnegie Mellon University revealed that 87% of all Americans could be uniquely identified using only three bits of information: ZIP code, birthdate and gender.
Detecting app leaks
imei works with the Wandera service that operates in the path of the data and inspects all outbound requests (from the device and inbound responses from the Internet) for risk. Sometimes those risks include malicious apps or phishing attacks. The risks identified in this report focus on the sensitive content that the apps and websites failed to protect adequately.
Learn more about app leakage by talking to the imei mobile security experts on 1300 65 77 99 and more about app leak research here.



